Headless APIs have been around in Salesforce B2C Commerce Cloud for a while now, under “OCAPI (Open Commerce API.).” And in 2020, a new set of APIs was added called the SCAPI (Salesforce Commerce API).
Within that new set of APIs, a subset was focused on giving developers complete control of the login process of customers, called SLAS (Shopper Login And API Access Service).
Now that was a lot of acronyms in a few sentences!
What is SLAS?
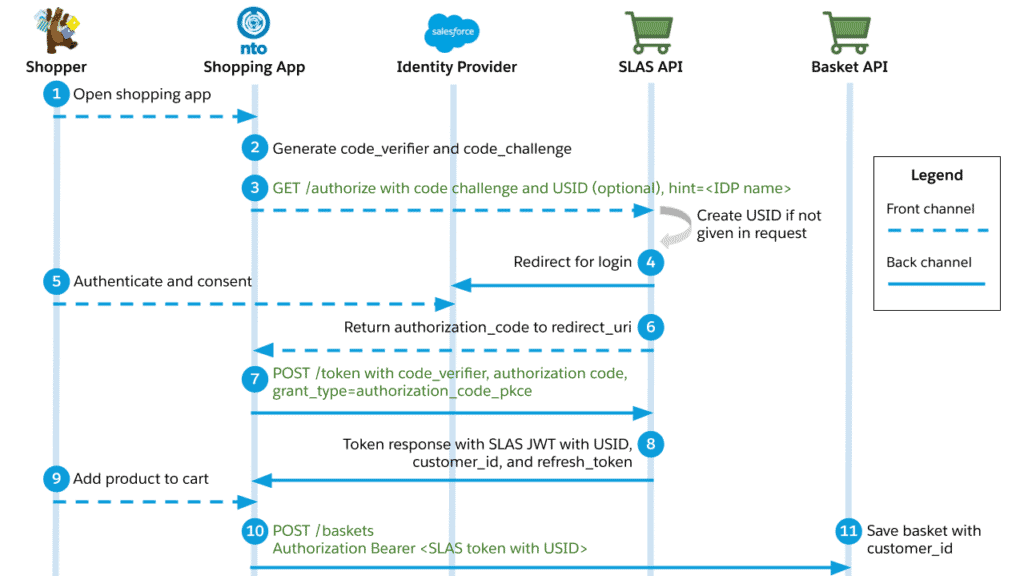
But what is SLAS, anywho? It is a set of APIs that allows secure access to Commerce Cloud shopper APIs for headless applications.
Some use-cases:
- Single Sign-On: Allow your customers to use a single set of log-ins across multiple environments (Commerce Cloud vs. a Community Portal)
- Third-Party Identity Providers: Use third-party services that support OpenID like Facebook or Google.
Why use SLAS?
Looking at the above, you might think: “But can’t I already do these things with SFRA and SiteGenesis?”
And in a sense, you are correct. The above login types are already possible within the current setup. But also ONLY within that setup, you can not use them for any other application you might have (endless aisle, kiosk, mobile app, …). You will have to build a custom implementation for each.
SLAS is a headless API and can be used by all of your channels, whether they are Commerce Cloud or not!
Besides that advantage, there are a few others!
Longer log-in time
People already familiar with Salesforce B2C Commerce Cloud will know that you only remain logged into the storefront for 30 minutes since your last interaction.
Many of my projects have requested this time be extended since this can be annoying, particularly in the checkout.
Until now, we could not extend the timeout customers experienced. With SLAS, we can extend that time to 90 days!
You read that right. A whopping three months increase to the other options!
Hybrid deployments
Another advantage is piggybacking on the Single Sign-On feature.
If you are already live on Salesforce B2C Commerce Cloud using SFRA or SiteGenesis, you can transfer sessions between channels more easily.
A good example would be a mobile application switching to the website or PWA-Kit to SiteGenesis, but keeping the session and basket alive in between!
How to use SLAS in SFRA?
In February 2022, Salesforce released a cartridge for SFRA to easily incorporate SLAS within your current set-up.
The cartridge brings all of the advantages of SLAS to SFRA, which is not headless but a monolithic set-up.
Disadvantages
As with all things, it comes at a “price.” If you install SLAS into your SFRA set-up, there are a few things to keep in mind:
- It uses headless APIs: This probably didn’t surprise you if you read the article. But this means you will be talking to “remote” APIs rather than talking to the server directly as you do with the standard Javascript APIs made available in the Rhino engine.
- Performance is impacted a little: Performance is affected since the cartridge adds three to four remote API calls to the flow. But we are talking about Salesforce services that abide by the same performance and uptime rules as the other Commerce services, so not something to worry about!
- Four extra API calls: You read it in the previous item, but four API calls are used (2 SCAPI and 2 OCAPI calls) to get the login and registration through SLAS to do its thing. This means you have 4 API calls remaining that you can do during the log-in procedure.
Security

It would be best to keep in mind that extending your logged-in period is not suitable for security.
Ninety days is very user-friendly but makes more sense in Mobile Applications than on your website. If someone logs in with remember-me on a public or shared computer, they will remain logged in for a long time with their details exposed.
This was, of course, their choice. But still, you want to protect people appropriately.
So maybe extending the logged-in period to a maximum of 1 or 2 days makes more sense? Discuss with your development, security and legal team how long you want to keep people’s sessions alive.
Can I use it in SiteGenesis?
Off course! It won’t be plug-and-play as with SFRA. But the code used isn’t rocket science, so you can use it as a cheat sheet to implement your version for SiteGenesis.
Should I use SLAS?
To answer this question, you need to look at your project and take the advantages and disadvantages of SLAS into account.
There is no clear-cut answer to this question. But that 90 days does sound attractive, doesn’t it?